You’ve probably heard about boosting online privacy by combining Tor with a VPN. “Tor over VPN” gets mentioned a lot in privacy circles. But does it actually make you safer? The truth is, for most users, it doesn’t—and it may even make you more trackable. This guide cuts through the noise with a technical, no-nonsense explanation.
Tor Over VPN Meaning
Tor over VPN means your internet connection first tunnels through your VPN provider and then routes through the Tor network. Your ISP only sees VPN traffic but has no clue you’re using Tor. Meanwhile, the Tor entry node doesn’t see your real IP—just the VPN server’s IP.

Technical Workflow:
- Device connects to VPN (all traffic is encrypted to the VPN server).
- VPN server forwards encrypted traffic into the Tor entry node.
- Traffic bounces through Tor’s relay network.
- Traffic exits through a Tor exit node onto the open internet.
Key Point: This setup hides Tor usage from your ISP but does not hide your IP from the VPN provider. Additionally, the Tor exit node still sees your destination traffic unless you’re using end-to-end encryption (HTTPS).
Do I Need a VPN Over Tor?
Short Answer: For almost everyone, no.
Tor is built from the ground up to provide anonymity without relying on external services. It routes your internet traffic through at least three separate nodes—an entry node, a middle relay, and an exit node.
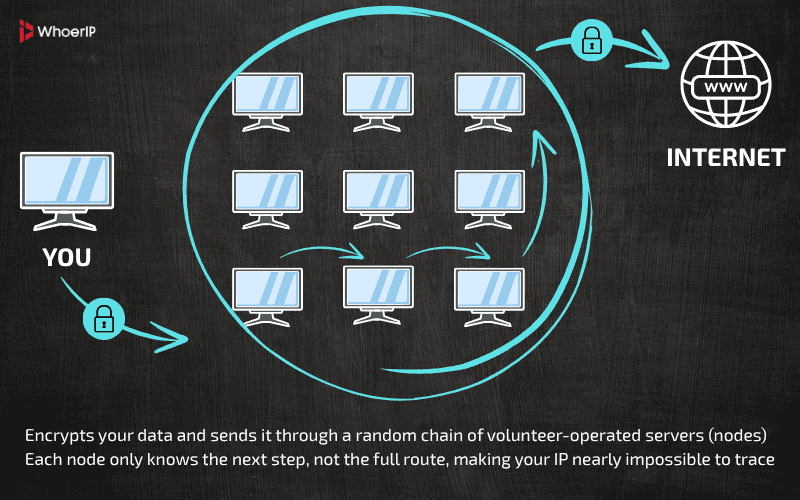
Each of these nodes only knows its immediate neighbors, so no single point has the full picture of your identity and activity.
When you add a VPN into the mix before Tor, you’re effectively handing your real IP address to the VPN provider. Now the VPN knows who you are, when you connected, and that you’re using Tor. If that VPN keeps logs, whether intentionally or under legal obligation, your privacy is compromised at the first step.
On top of that, VPN IP addresses are easily identifiable to network observers. Some surveillance systems and governments actively monitor known VPN ranges. Instead of blending into the noise of regular Tor users, you’re now part of a much smaller, more conspicuous group—people who are tunneling Tor through a VPN. That alone can make your traffic more interesting to advanced adversaries.
Adding a VPN also doesn’t improve Tor’s encryption. Tor already encrypts your traffic three times within its network. The VPN only adds encryption between your device and the VPN server, which doesn’t enhance the core anonymity Tor offers.
Risks with Tor Over VPN:
- Adds a single point of trust: the VPN.
- Increases your attack surface. Some nation-state adversaries monitor VPN IP blocks. Using VPN + Tor can actually make your traffic stand out.
- False sense of security. The VPN sees your real IP, and Tor doesn’t inherently become stronger.
- Performance degradation. VPN encryption overhead plus Tor’s multi-hop latency results in painfully slow connections.
Valid Use Cases:
- Circumventing Tor censorship (if Tor is blocked by your ISP).
- Obscuring Tor usage from authoritarian ISPs.
Iptables Tor Over VPN Setup
If you still choose Tor over VPN, enforcing it via firewall rules is crucial to prevent leaks.
iptables Example Setup:
# Flush existing rules
iptables -F
iptables -t nat -F
# Accept traffic through VPN tunnel
iptables -A OUTPUT -o tun0 -j ACCEPT
# Drop traffic outside VPN
iptables -A OUTPUT ! -o tun0 -j DROP
# Allow loopback
iptables -A OUTPUT -o lo -j ACCEPTVerify:
- Use
ip ato confirmtun0is active. - Check leaks with DNS tools and IP checkers.
- Do not start Tor unless VPN tunnel is verified active.
VPN Over Tor vs Tor Over VPN
| Feature | Tor over VPN | VPN over Tor |
|---|---|---|
| First Connection Point | VPN | Tor |
| ISP Sees | VPN traffic only | Tor traffic |
| VPN Sees | Your real IP | Tor exit node IP |
| Bypass Tor Blocks | Yes | No |
| Access .onion Sites | Yes | No |
| Speed Impact | High (VPN + Tor latency) | Very High (Tor first, then VPN) |
| Setup Complexity | Medium | Complex |
Key Insight:
- Tor over VPN only hides Tor usage from your ISP but compromises privacy to the VPN.
- VPN over Tor hides VPN usage but breaks access to .onion services and is extremely slow.
Best Free Tor Over VPN Setup
Avoid free VPNs. They frequently monetize by selling user data, defeating the purpose entirely.
Safer Practice Checklist:
- Use a VPN with a transparent no-logs policy.
- Combine only if Tor access is censored in your country.
- Verify with DNS leak tests (check your IP on our site).
- Use bridges or pluggable transports instead if Tor is blocked—safer than Tor over VPN.
The Tor Project itself does not recommend Tor over VPN for ordinary users. Their design already assumes adversaries may observe entry and exit traffic but cannot correlate it.
Pro Tip: If you’re concerned about hiding Tor usage from your ISP, consider Tor bridges instead of a VPN. Bridges are designed exactly for this purpose without introducing trust in a VPN provider.
Tor over VPN sounds good in theory but rarely makes practical sense for privacy. It introduces a trusted third party (the VPN) into a system designed to avoid trust. Unless you’re evading censorship, you’re better off using Tor alone, configured correctly with security best practices. Confirm your setup by checking your IP to ensure no leaks.
Frequently Asked Questions
Why choose Tor over VPN?
You might opt for Tor over VPN if your internet provider blocks access to the Tor network or if you simply don’t want your ISP to know you’re using Tor. In this setup, your ISP only sees that you're connected to a VPN, not Tor itself. However, this comes with a serious trade-off: you’re now placing trust in the VPN provider, which has direct access to your real IP address.
Why would someone prefer Tor over VPN?
Primarily, it's about censorship circumvention. If you live in a country where Tor connections are blocked or heavily scrutinized, routing Tor through a VPN allows you to bypass these restrictions. The VPN masks your Tor usage. But it's crucial to understand—this does not improve your anonymity within the Tor network. In fact, it slightly weakens it by adding a trusted intermediary (the VPN). For anyone not dealing with heavy censorship, using Tor directly is safer, simpler, and aligns better with how Tor is designed to protect your privacy. For more guides, check out: How to check your IP How to hide your IP address How to change IP on Mac OS
Do I need a VPN over Tor?
Not usually. Tor already anonymizes your traffic. A VPN on top may add a layer, but it can also slow things down or reduce anonymity if misconfigured.
VPN over Tor vs. Tor over VPN
Tor over VPN: Safer for beginners. Hides Tor from your ISP. VPN sees your activity. VPN over Tor: More complex. Your VPN runs inside the Tor network. Hides VPN use from Tor, but setup is trickier.
Using Tor over VPN
This is the most common setup. Connect to your VPN, then launch Tor. Your IP is masked by the VPN, and Tor gives layered encryption.
















